How to Scan a Website Using Nmap
When people think about Nmap, they usually picture network scans. But Nmap is also a powerful tool for gathering information about websites. You can use it to:
- Find open services
- Analyze SSL configurations
- Detect server technologies
- Discover potential vulnerabilities
In this guide, I go over how to use Nmap to scan a website.
How to Perform a Basic Website Scan
The easiest way to start scanning a website with Nmap is by simply pointing it at the domain name. Nothing fancy; just a quick sweep to see what’s exposed.
You can run:
1
nmap example.com
This basic scan will:
- Look up the IP address behind the domain.
- Check if the server is reachable.
- Scan the most common 1,000 TCP ports to find out which ones are open.
- Guess what services are running based on the ports it finds.
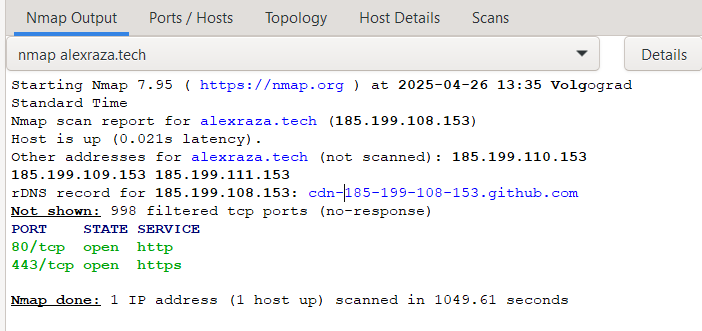
Example Output:
As you can see, a quick scan of my website domain (alexraza.tech) only revealed two open ports: 80 for HTTP requests and 443 for HTTPS requests. This is standard for most websites.
A basic scan like this gives you a quick look at what the server is offering to the world. Even if a website looks simple from the outside, a scan might reveal hidden services running in the background and things that could be interesting (or vulnerable).
If you don’t get any results, it doesn’t always mean the server is “clean.” Sometimes firewalls block scans or hide services. In those cases, you might want to tweak your scanning options to get around basic defenses.
More Focused Scanning Options
If you want to focus your efforts a little more, here are some simple ways to get better information without overwhelming yourself.
1. Scan Only Common Web Ports
1
nmap -p 80,443 example.com
If you add the -p 80,443 option, you tell Nmap to check only specific ports instead of scanning the default list of 1000. Port 80 is for regular web traffic (HTTP) and port 443 is for secure web traffic (HTTPS). By scanning only these, you save time and focus directly on what most websites are using.
This is useful if you are just interested in the public website and do not care about background services like SSH or FTP.
2. Service Version Detection
1
nmap -sV example.com
Adding -sV makes Nmap not only find open ports but also try to figure out exactly what is running behind them. For example, it might tell you the web server is Apache 2.4.7 or Nginx 1.14.0.
If a server is running an outdated version of software, it might have known vulnerabilities. Attackers often look for these weak points because they can be exploited easily if the server is not patched.
3. Detect Operating System
1
nmap -O example.com
Using -O tells Nmap to try to guess the operating system behind the server based on how it responds to different network probes. You might find out it is running Linux, Windows, or something more exotic.
This feature does not always work because many servers are protected by firewalls or security systems that block the fingerprints Nmap looks for. Still, when it works, it gives you extra context about the environment.
4. SSL/TLS Scan
1
nmap --script ssl-enum-ciphers -p 443 example.com
This command goes a step deeper. It uses a special Nmap script called ssl-enum-ciphers to analyze the security settings on the HTTPS port (443). It checks what encryption methods the server accepts and whether any of them are outdated or weak.
Websites need strong encryption to protect user data. If a server is still accepting old protocols like SSLv3 or using weak ciphers, attackers could intercept or manipulate the traffic. This type of scan helps you spot those risks early.
What You Can Do with Website Scan Results
Once you finish scanning a website, you will have a small but important map of what the server looks like from the outside. Here are some practical things you can do with the information you gather:
Identify weak services: If you find services like FTP or Telnet open, that could be a sign the server is using old or insecure protocols. These are easier to exploit because they do not encrypt traffic and often have weak authentication.
Find old or vulnerable software: When you use the -sV option to discover service versions, you can then check if that version has known vulnerabilities. Old software is a common way attackers gain access.
Analyze SSL security: If you run an SSL scan, you might find the server accepts weak ciphers or outdated encryption protocols like SSLv3. This is a warning sign because weak SSL settings leave users open to attacks like interception or data tampering.
Discover additional services: Web servers sometimes host more than just a homepage. You might find admin panels, hidden APIs, old test sites, or other applications. These are often not well secured and can be great starting points for deeper testing.
Prioritize testing: With a list of open services and technologies, you can plan your next steps instead of randomly poking around. Focus on services that seem out of place, outdated, or unnecessary for a normal public-facing server.
Finding Vulnerabilities to Exploit
If you discover an open service or software version, you can look up known vulnerabilities related to it. There are a few ways to do this:
Search online: Websites like Exploit-DB and CVE Details list known vulnerabilities. You can search using the service name and version number you found.
Use Metasploit: Metasploit contains a library of ready-to-use exploits. Once you know what version of a service is running, you can search inside Metasploit using commands like:
search apache 2.4.7. If an exploit is available, Metasploit can sometimes automate the process of using it to gain access or demonstrate the risk.
Deeper Website Scanning: Advanced Options
To help you dig even deeper into how a website is set up and where potential weaknesses might hide, Nmap has a powerful feature called Nmap Scripting Engine (NSE).
NSE allows you to run pre-built scripts that can automate checks for vulnerabilities, misconfigurations, and even common files or hidden directories.
Nmap scripts are grouped into categories like:
vuln(for known vulnerabilities)auth(for authentication bypass checks)discovery(for finding services and files)safe(for scripts that are unlikely to cause disruptions)
You can find a list of all available scripts on the official Nmap website at nmap.org/nsedoc/. Each script there is explained along with what it does and when to use it.
When you are scanning a website, you can target just HTTP-related scripts by using patterns like http-*. This limits the scan to scripts meant for websites and web servers.
Now let’s look at some practical examples.
1. Check for Common Vulnerabilities
You can run specialized Nmap scripts to check for vulnerabilities on HTTP services.
1
nmap --script http-vuln* -p 80,443 example.com
This tells Nmap to run any vulnerability detection script that starts with “http-vuln”.
Example vulnerabilities it might find:
- Sites using default credentials that attackers could easily guess
- Open redirects that allow an attacker to redirect users to malicious sites
- Path traversal vulnerabilities where an attacker could access restricted files outside the intended web folders
Finding these types of flaws early is important because many automated attacks on websites focus on simple but damaging issues like these.
2. Full HTTP Enumeration
Get more information about how the web server is configured:
1
nmap --script http-enum -p 80,443 example.com
This script tries to find common folders and files by requesting them and seeing if the server responds. It looks for things like:
- Admin panels
- Login pages
- Upload forms
- Backup files
- APIs and endpoints
Finding hidden or forgotten areas of a site can be extremely useful when doing a security review or penetration test. They often have less protection than the main public-facing areas.
3. SSL Certificate Analysis
You can gather details about the SSL certificate itself:
1
nmap --script ssl-cert -p 443 example.com
This shows:
- Who issued the certificate
- Validity dates for the certificate
- Public key size and algorithm used
This helps you check if the website is using modern, secure encryption. Old, short keys or outdated algorithms like SHA-1 are warning signs that security might need updating.
Example: Deep Website Scan Command
Here is an example of a command that combines some of these options:
1
nmap -sV --script http-enum,http-vuln*,ssl-enum-ciphers,ssl-cert -p 80,443 example.com
It will:
- Detect service versions
- Enumerate web directories
- Search for HTTP vulnerabilities
- Analyze SSL configurations
This gives you a much more complete picture of the site’s security.
Final Thoughts
Scanning websites with Nmap is a simple but incredibly powerful way to collect information that can guide your security testing or auditing efforts.
By choosing the right options and scripts, you are not just checking for open ports. You are learning about the server’s structure, the technologies it uses, the security measures in place, and sometimes even the mistakes left behind by misconfiguration or neglect.
Each scan gives you a clearer picture of the website’s “footprint”: what services it exposes to the world, how securely it handles traffic, and whether there are areas that might need a closer look.
Once you know the basics, you can build on this knowledge and move into more advanced techniques like vulnerability scanning, service fingerprinting, and even automated exploitation with the right ethical boundaries.